Are You Ready to Witness the Future of Data Security?
Platform
©2025 QuNu Labs Private Limited, All Rights Reserved.
Armos - Quantum Key Distribution (QKD) is a state-of-the-art appliance which provides unconditional security for your critical data by leveraging the principles of quantum physics.
Armos - Quantum Key Distribution (QKD) is a state-of-the-art appliance which provides unconditional security for your critical data by leveraging the principles of quantum physics.
Today’s complex network infrastructure has been built over time and each of the devices have a specific role to play. With such complexities being a reality, Armos quantum key distribution (QKD) can be deployed in any present cryptographic system.
The quantum layer sits on top of the existing network, making the deployment and adoption seamless - be it a data centre or a hybrid model.
Quantum key distribution (QKD) uses quantum physics to securely distribute encryption keys. Armos (QKD) transmits keys using randomly generated photons over a fiber cable. These photons, in a quantum state, exchange quantum information to establish the same key at both ends.
QNu's Armos (QKD) delivers quantum keys that ensure unconditional security for two parties communicating securely, based on quantum physics. It detects eavesdroppers, providing secure symmetric key distribution for encrypting confidential data.
Any attempt to read photon information causes errors and collapses the keys, halting generation and alerting the admin. Key generation resumes when errors decrease. The key is never exchanged, making eavesdropping nearly impossible. The symmetric key remains a shared secret.
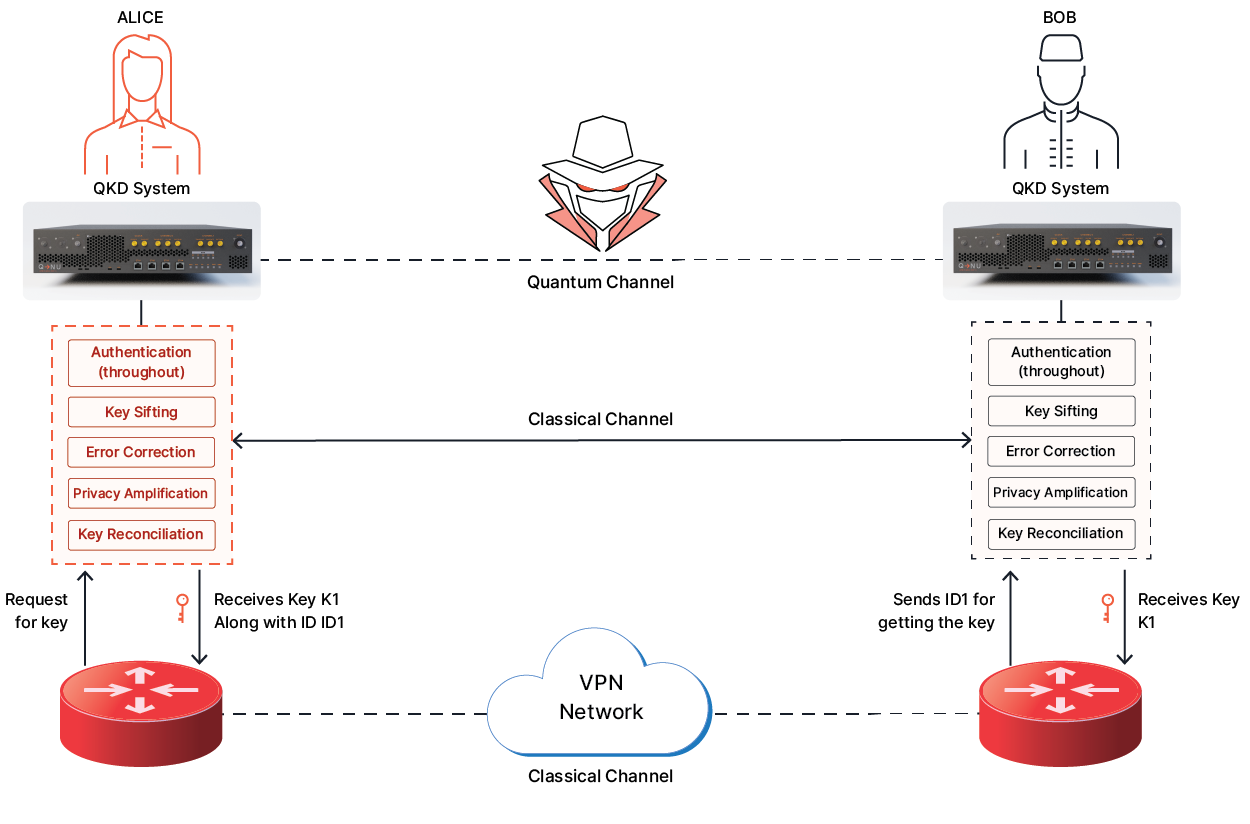
Armos QKD enables to create secure encryption keys for any two ends of a communication link for Symmetric Key Encryption system without ever sharing the actual keys on any links.
Quantum cryptography is the wider field of applying quantum mechanical properties for cryptographic purposes. QKD is the most mature and widely deployed application, specifically focused on secure key distribution. While quantum cryptography encompasses various quantum-based security techniques, QKD remains the most commercially viable with 30+ QNu deployments globally.
QNu's Armos QKD system achieves 150-200 km point-to-point, significantly exceeding the industry standard of 80-100 km. To extend beyond these distances, organisations deploy trusted node networks. QNu's 500 km intercity network demonstrates this scalability with only 4 nodes vs 10 for competitors, achieving 60% infrastructure reduction.
QKD costs have reduced significantly. While initial hardware asset investment is higher than traditional encryption, the total cost of ownership is competitive considering long-term security value and QNu's 60% infrastructure reduction. For defence, government, and high-security applications shielding data with 20-30 year confidentiality requirements, QKD is cost-effective.
Yes, QKD works over standard single-mode optical fibre used in telecommunications networks. Organisations don't need to lay new fibre infrastructure. QNu's 500 km network was deployed over existing optical fibre infrastructure in Rajasthan, demonstrating seamless integration. This means if you have fibre between locations, you can likely deploy QKD without additional fibre investment.
If QKD detects eavesdropping (via abnormal quantum bit error rates), it instantly discards compromised bits and alerts security teams—no communication continues with a risky key. The system then generates a new secure key using fresh quantum states. Continuous monitoring enables real-time threat detection, making automatic intrusion detection QKD’s key advantage over traditional encryption. QNu’s systems also provide detailed logs and alerts, integrating with SOC and SIEM platforms for enterprise-wide visibility
QKD integrates with existing cryptographic infrastructure through standard key management interfaces. It generates quantum-secure symmetric keys for conventional encryption systems like AES or one-time pads, ensuring current applications and network equipment function as usual—just with stronger keys. QNu’s solutions support standard APIs such as KMIP and PKCS#11 for seamless integration with HSMs, encryption appliances, and key management systems. The quantum advantage lies in secure key distribution, not infrastructure replacement. Deployment involves installing QKD endpoints, connecting them via fiber, and configuring key management—typically completed within days to weeks depending on scale.
No, quantum computers cannot break QKD—its fundamental advantage. Unlike RSA/ECC, which rely on mathematical complexity quantum computers shatter via Shor's algorithm, QKD's security stems from quantum physics: the no-cloning theorem prevents state copying, and Heisenberg's uncertainty principle detects any measurement disturbance. These are unbreakable laws of nature, not computational puzzles. Quantum computers even enhance QKD via repeaters, making it the ultimate quantum threat defense.